Is your client’s industrial control system (ICS) becoming a liability to their operations? Learn how to effectively plan and execute a successful ICS replacement.
Learning objectives
- Understand the importance of effective planning for successful industrial control system (ICS) replacement (or replacement implementation).
- Develop an understanding of the key elements of a control system replacement.
- Identify the characteristics of a modern ICS.
- Understand the importance of ICS cybersecurity.
ICS insights
- Industrial application owners face significant challenges as they seek to enhance the security, reliability and resiliency of their control systems. To address these issues, many are adopting master planning methodologies, such as front-end loading, commonly known as FEL), to identify and mitigate vulnerabilities.
- Findings from current state assessments frequently reveal security and reliability risks prompting many organizations to pursue comprehensive system asset replacements and architecture upgrades. Understanding the key elements and sequencing of a control system replacement is essential to planning for successful implementation.
A modern industrial control system (ICS) is founded on technology that evolves over time due to product life cycle, advances in technology and owner needs. As discussed in the July 2024 article, “Know whether it’s time to replace a control system,” completing a current state assessment will help engineers determine the status of an owner’s control system. A current state assessment helps identify vulnerabilities and aids in determining if a system is ready for replacement.
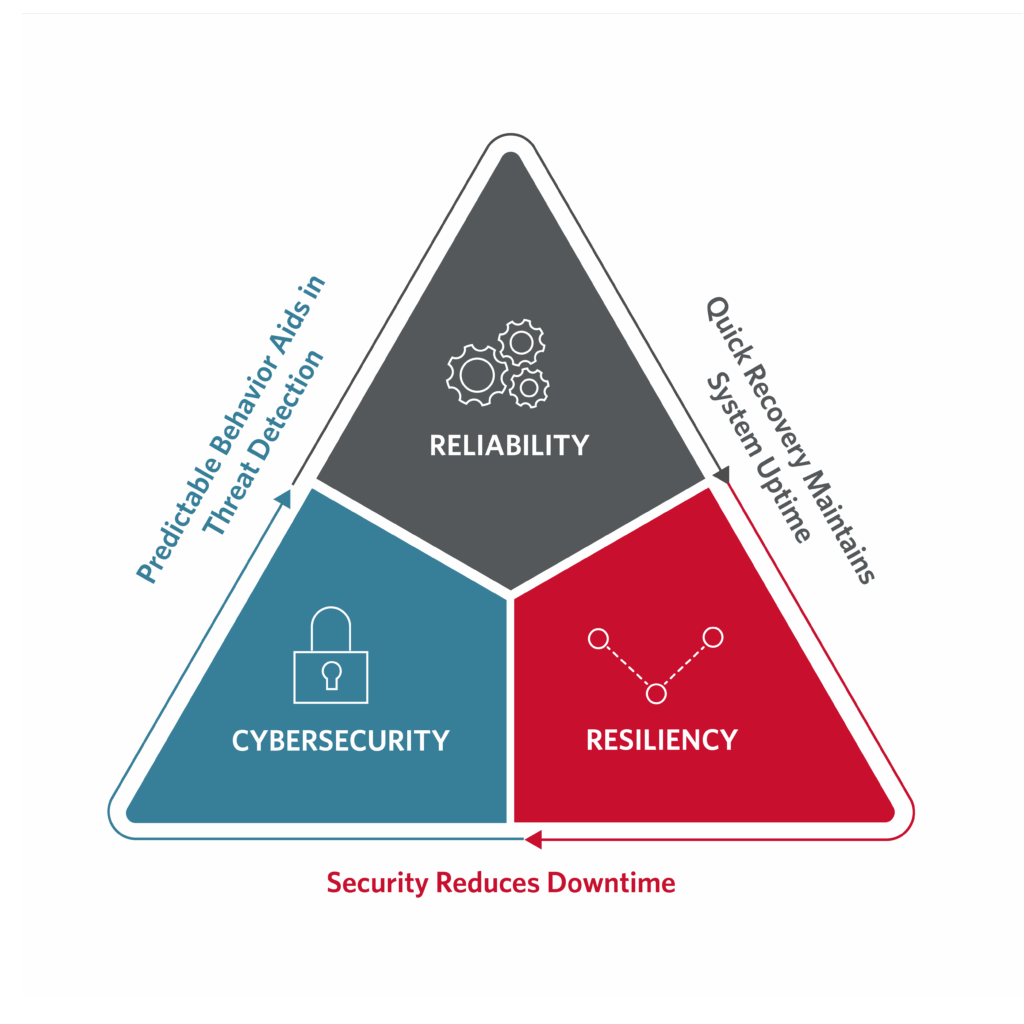
Common vulnerabilities identified by most system owners represent risks to the security, reliability and resiliency of their operations (see Figure 1). If left unmitigated, this may result in varying consequences depending upon the industrial applications (see Figure 2).
Once a current state assessment of the system is complete and it’s decided that a replacement is required, the team will begin the process of pre-project planning.
What are the key elements of an ICS replacement?
Replacing a control system in an operating industrial application is a significant undertaking. Through effective planning and vulnerability management, the system replacement can mitigate identified risks during the current state assessment, while fostering a scalable solution that enhances operational efficiency, aligns with cybersecurity best practices, and strengthens system reliability.
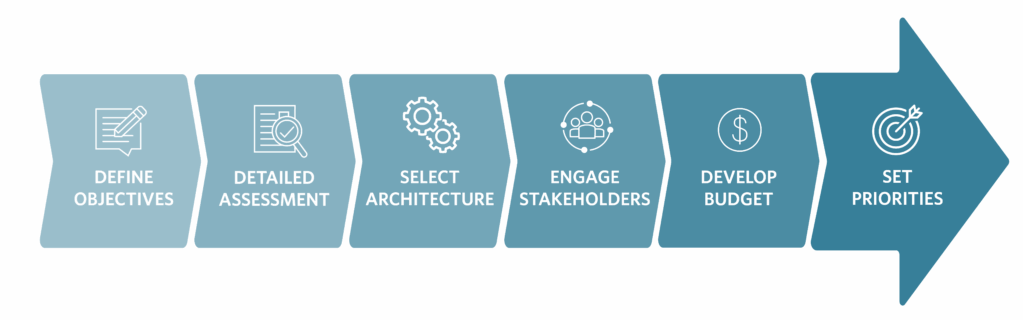
To ensure success, it is essential to understand and address the key elements involved in a control system replacement (see Figure 3). These six elements form the foundation of a well-planned, executed and future-ready upgrade.

Establish clear objectives
Before developing the technical details, it is essential to define the goals of the replacement strategy. Are you aiming to eliminate outdated hardware or software, migrate from proprietary equipment, increase the data footprint, improve communications or integrate with modern technologies? Will system downtime be permitted or will cutovers be required to be sequenced with ongoing operations?
These objectives will determine the scope of the replacement strategy and will guide every subsequent decision, from the selection of the system architecture to setting the budgets. Without these guiding principles, the project risks becoming unfocused, leading to unnecessary costs, rework and delays.
Complete detailed assessment
Although the decision to replace the system has been made, a thorough understanding of the existing setup is required. Using the vulnerabilities identified during the current state assessment as a baseline, document the following:
- Architecture: Number and location of network nodes and single points of failure.
- Data: Data flow and integration with information technology (IT) systems.
- Communication: Media, protocols and virtualization.
- Hardware: Manufacturer, model, configuration, available spares or stock.
- Software: Version, service packs, patches and licensing.
- Documentation: Record drawings, control descriptions and owner standards.
Use this as an opportunity to identify any pain points that may represent an emergent or imminent operational reliability concern or high cybersecurity priority.
Much of this information may have already been collected during the current state assessment. This step is crucial as it will inform the level of effort for replacement activities downstream of pre-project planning. For example, if validated control descriptions are not available, then the plan will require the step of code analysis and reverse engineering the strategies for programming of the new system. This can represent an extensive effort proportional to the system size and complexity of system architecture.
This assessment ensures the replacement approach addresses current system shortcomings while maintaining long-term compatibility where necessary.
Select the right architecture
Choosing the right system architecture is one of the most critical steps in the replacement process as it will be the basis for a new system. The modern ICS can often include a combination of:
- Distributed control systems (DCS)
- Programmable logic controllers (PLC)
- Original equipment manufacturers
- Equipment, human-machine interfaces (HMI)
- Operator interface terminals (OIT)
- Robust communication networks
The selected architecture should align with the owner’s operational goals, support phased build-out, support scalability for future needs and comply with industry standards for reliability and cybersecurity. Decisions such as centralized versus distributed control or on-premises versus cloud-based data management should be evaluated based on the unique demands of the owner’s operations.
It is also important to establish the requirement for interim system architectures to support temporary controls and parallel network standup, which is common for replacements in operating facilities.
Engage stakeholders
Control system replacements affect multiple users and owner departments, including engineering, operations, maintenance, IT and management. Engaging all stakeholders early in the planning process ensures each member has a voice and that their needs and concerns are addressed. Collaborating across teams helps define requirements, prevent misunderstandings and gains buy-in for the project. Early engagement fosters a sense of ownership and establishes smoother transitions during implementation.
Develop a realistic budget and schedule
Budgeting for a control system replacement involves more than just hardware and software costs. Consider additional factors such as software analysis, engineering design, operability studies, construction/installation, system integration, training and ongoing maintenance. It is also wise to guide the owner or operations team to allocate contingency funds for unforeseen challenges that may arise during implementation. It is common for control system replacements to take years to complete depending upon the project scale and objectives. Therefore, allocating budgets to include material and labor escalation through the midpoint of construction to account for a rise in costs as the replacement is implemented is good practice.
Planning-level scheduling helps establish expectations for project duration. Ensure that adequate time is included for stakeholder discussions, engineering design, review periods, permitting, regulatory coordination, as well as testing and commissioning.
A realistic budget and schedule typically help avoid financial strain and unrealistic expectations, allowing the project to proceed without compromise.
Prioritize cybersecurity
As the need for data grows, the attack surface of control systems can grow, requiring diligence to mitigate vulnerabilities that expose owners of industrial applications to cyberthreats. Attackers can exploit outdated software, obsolete hardware and unsecured networks to disrupt operations. Often, security of the systems is the primary driver requiring a system replacement.
Engineers and controls experts should guide owners to prioritize investments in cybersecurity to incorporate robust measures into the design of the new system. Compliance with industry standards and best practices, such as NIST 800-82 and IEC 62443 is essential to protect your control system assets and maintain operational cybersecurity.
By understanding and addressing these key elements as you complete pre-project planning, you are establishing a foundation for the success of the control system replacement.
Modern ICS architecture
Understanding modern ICS characteristics will help consultants establish the overall system architecture that is appropriate for a client’s operational needs.
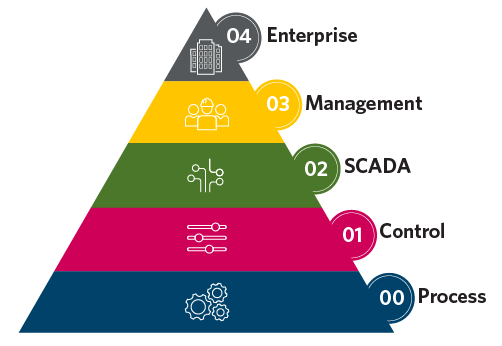
The modern ICS can be visualized as a hierarchical stack with levels from physical processes at the bottom to enterprise integration at the top (see Figure 4). This model is a simplified version based upon the Purdue Enterprise Reference Architecture, which serves as a foundation model for designing and understanding ICS. A modern ICS, designed with this model in mind, emphasizes seamless integration, data flow and operational efficiency across all levels.

Level 0: Physical process: The foundational level of all control systems is the process. This is where the advanced sensors and actuators interact with the physical process. Modern characteristics include:
- Sensors and devices: Hardwired or networked enabling interface for local data processing, communication for process measurement and control actuation.
- Process networks: Devices are increasingly networked supporting real-time data exchange and remote diagnostics for process control and industrial internet of things (IIoT) integration.
- Power monitoring: Advanced components support monitoring of energy usage that can be trended over time to support efficient and sustainable operations.
- Manual controls: Ability to manually control certain processes independent of control system availability during emergencies.
Level 1: Basic control: The next level focuses on interfacing instruments and devices with equipment such as PLCs or DCS controllers, which manage the monitoring and control of the physical process. Characteristics for modern systems include:
- Processing: Controllers use onboard central processing units to monitor large datasets in real-time and can execute complex control algorithms. Communication processors are responsible for managing the exchange of data directly between devices within a network.
- Redundancy: Critical processes may include solutions to reduce downtime and improve resiliency using hot-swappable modules, uninterruptible power supplies and redundant components where high availability is required. OITs provide local operational view and control interface if the network backbone is unavailable.
- Interoperability: Support for multiple communication protocols, such as Common Industrial Protocol (CIP), Modbus, Distributed Network Protocol (DNP3), Open Platform Communications Unified Architecture (OPC UA) and Building Automation and Control Network (BACnet) for compatibility with a diverse selection of devices and manufacturers.
Level 2: Supervisory control: Supervisory control and data acquisition (SCADA) systems and HMIs are responsible for monitoring and controlling processes. Modern characteristics include:
- Situational awareness: Intuitive and user-friendly HMIs allow operators to quickly interpret data through the use of graphical elements.
- Alarm management: Intelligent alarm systems that prioritize alarms based on a pre-defined operations response time. This allows for a first-in, first-out method to effectively mitigate nuisance alarm storms due to cascading alarms.
- Mobility: Operators can monitor and control systems from anywhere they have authorized access using secure, remote tools.
- Data-driven insights: Real-time analytics and visualization tools enable proactive decision-making.
Level 3: Operations management: This level bridges ICS and IT, focusing on process optimization and production workflows. Modern features include:
- Manufacturing execution systems (MES) integration: MES provides real-time production tracking, scheduling and quality management.
- Intrusion detection: Monitoring of control system network with notification of possible cyber events.
- Advanced analytics: Predictive and prescriptive analytics tools leverage data to improve efficiency and reduce downtime.
- Tiered historical data: Replicated historical SCADA data for management reporting and integration with enterprise systems.
- Web services: Support for replication of SCADA applications for remote viewing and interaction.
- Cybersecurity: Secure communication channels and access controls protect sensitive production data.
Level 4: Enterprise: At the top of the stack, enterprise systems such as enterprise resource planning and computerized maintenance management systems connect operational data with the business functions like asset management, finance, inventory and supply chain. Modern ICS characteristics include:
- Seamless IT/operational technology (OT) integration: Unified data flows ensure operational data informs business decisions in real time.
- Cloud connectivity: Cloud platforms enable centralized data storage, analysis and collaboration.
- Scalability: Enterprise-level systems support growth and accommodate new technologies.
- IT/OT isolation: Ability to separate from the operations management level in the event of a cyberattack on the enterprise to avoid disruption to operations.
A control system replacement presents an opportunity to implement improvements, thus aligning vulnerable systems and critical infrastructure with industry standards. Taking time during the planning process to define a system architecture that balances risk and financial management is a beneficial practice to achieve the objective of overall system reliability.
Control system replacements are an inevitable reality from the time they are commissioned. A control system replacement can be achieved over time as part of a maintenance and renewal program. However, many owners reach a point where their control systems have become a liability requiring major investments to fix. Often large-scale replacement is the solution.
Planning for the design and replacement of a control system is essential. Without proper preparation, the replacement process is likely to incur higher costs and longer timelines, while exposing the owner’s operations to potential risks from unresolved vulnerabilities.
Once the designer and owner have completed the planning process, considering the key elements of a control system replacement, the team will be ready to move into the design phase of the project.